Security researchers from Dr.Web have identified a new family of Android trojans that significantly raises the threat level by integrating machine learning technology. Unlike older malware that relied on fixed scripts, this new strain uses Google’s TensorFlow.js to perform visual analysis, allowing it to detect and click advertisements in a way that closely mimics real human behavior. As a result, many traditional ad fraud detection systems struggle to identify its activity.
This malware is being distributed through GetApps, the official app store for Xiaomi devices, where it disguises itself as popular games. Reported examples include titles such as Theft Auto Mafia with more than 61,000 downloads, as well as Cute Pet House and Creation Magic World. During initial installation, these apps appear harmless, but malicious components are later delivered through app updates, allowing the malware to bypass early store security checks.
One of the most alarming features is a mechanism known as Phantom mode. In this mode, the malware secretly launches an invisible WebView browser that the user cannot see. It captures screenshots of the hidden browser and sends them to an AI system that analyzes the screen to locate advertisement buttons and perform clicks automatically. In addition, a Signalling mode uses WebRTC technology to stream a virtual screen back to hackers, enabling real-time remote control of the device, including scrolling and typing, without the owner’s knowledge.
Although this type of click fraud malware does not directly target personal data, its impact on users is still severe. Infected devices experience noticeably faster battery drain, reduced performance due to background AI processing, and potentially higher internet usage costs caused by continuous loading of ads and video content.
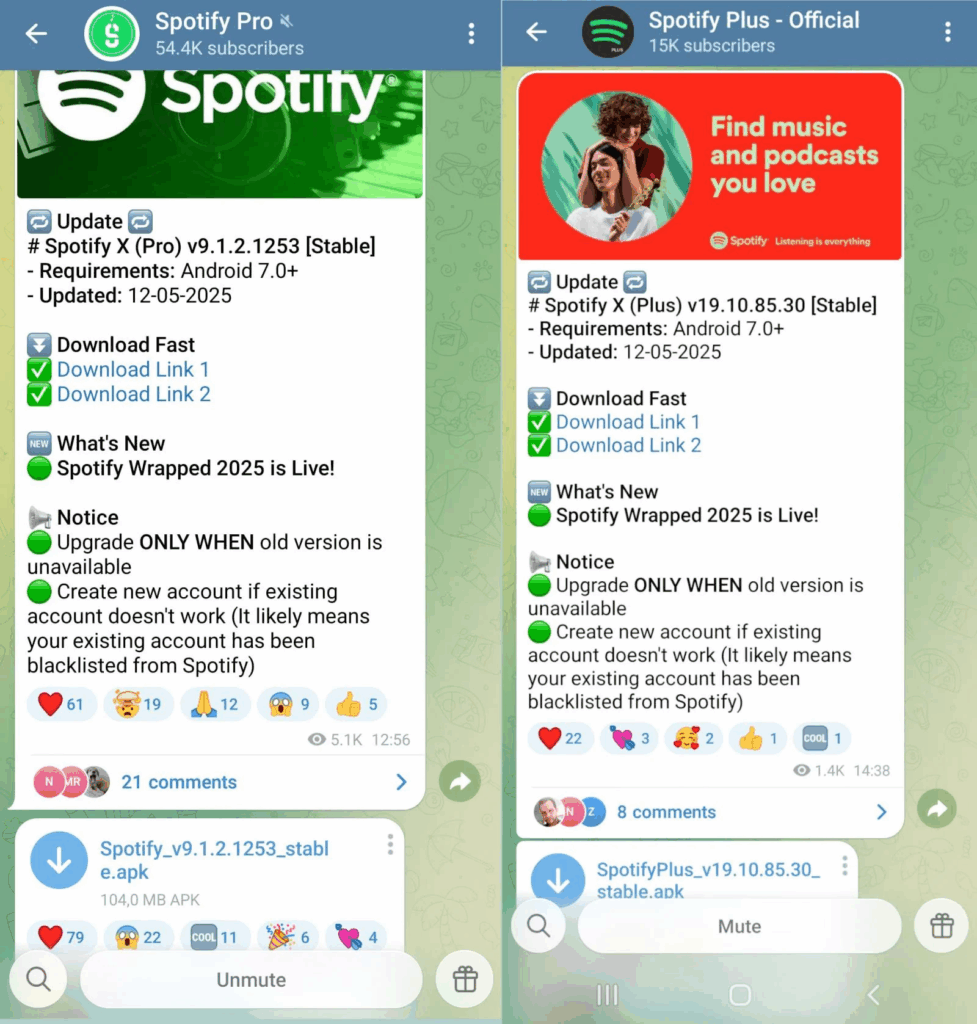
Beyond official app stores, the malware is also spreading aggressively through modified apps and unofficial distributions shared on third-party websites or Telegram channels. Examples include altered versions of Spotify or ad-free YouTube apps. Researchers note that these apps often function exactly as advertised, which lowers user suspicion. While users enjoy music or videos, the AI malware operates silently in the background, generating income for attackers.
For maximum protection, users are strongly advised to avoid installing apps from unknown sources or modified applications that promise free premium features. Regularly checking battery usage statistics in device settings is also recommended. Apps that consume unusually high power despite minimal use may be a warning sign that AI-powered malware has already compromised the device.
Source: BleepingComputer