Hackers Exploit Email Configuration Flaws to Send Convincing Phishing Emails, Microsoft Warns
Microsoft has released a new and concerning threat intelligence report, warning that cybercriminals are actively exploiting weaknesses in email routing and domain anti-spoofing configurations. By taking advantage of improperly secured email systems, attackers are able to send phishing emails that appear to come directly from within the same organization, making them far more convincing to employees.
This attack method significantly increases the likelihood of success, as recipients often believe the emails are legitimate internal communications from colleagues or company departments. As a result, credential theft has become one of the primary outcomes of these campaigns.
Phishing Activity Rising Since Mid 2025
Microsoft reports that this attack pattern has been steadily increasing since May 2025. Threat actors commonly rely on Phishing-as-a-Service platforms, such as Tycoon2FA, to rapidly deploy large-scale phishing campaigns. These services allow attackers to easily generate a wide range of deceptive email templates.
Common lures include fake voicemail notifications, realistic SharePoint document sharing alerts, and IT messages claiming that a user’s password is about to expire. These tactics are designed to create urgency and pressure victims into entering their login credentials on fraudulent websites.
Internal-Looking Emails Bypass Filters and Users Alike
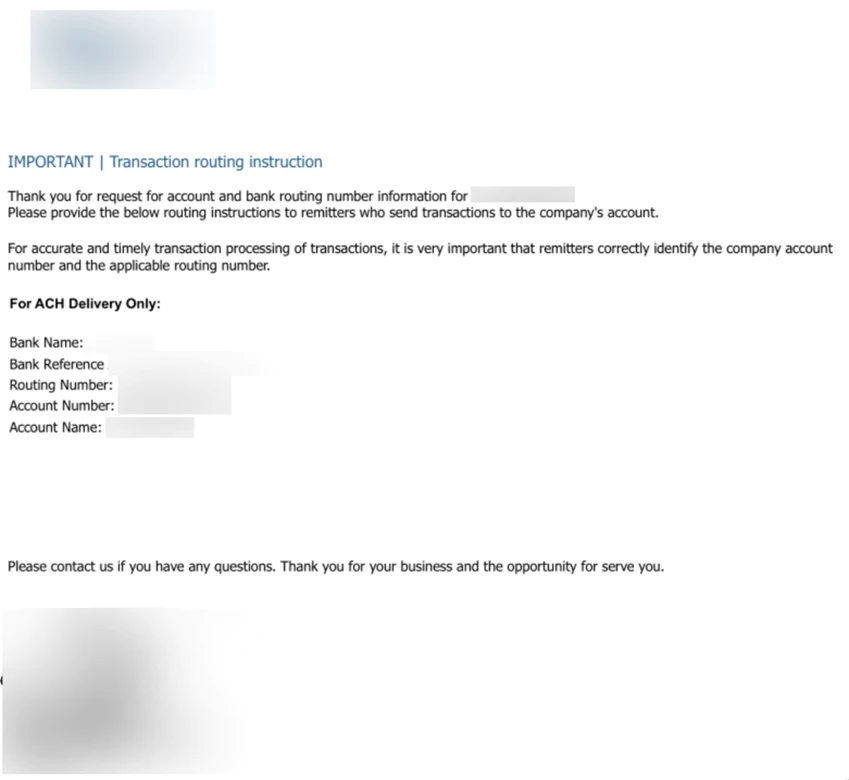
According to Microsoft, these phishing campaigns do not target a specific industry. Instead, they broadly scan for organizations with weak email security configurations. The most alarming aspect is that the emails display both sender and recipient addresses using the same domain, making them appear indistinguishable from genuine internal emails.
This similarity allows many standard spam filters to overlook the messages, while employees themselves struggle to recognize the deception. As a result, attackers gain a powerful entry point into corporate systems.
Beyond Credentials, Financial Fraud Is Also a Risk
In addition to stealing account passwords, attackers are also using this technique for business email compromise scams. By impersonating executives or finance departments, hackers attempt to trick organizations into transferring money using fake invoices or payment requests.
Microsoft warns that organizations without properly enforced DMARC, SPF, and DKIM policies face a significantly higher risk of financial loss. In many cases, recovering stolen funds from these attacks is extremely difficult once the transfer is completed.
Misconfiguration, Not a Direct Microsoft 365 Vulnerability
Microsoft emphasized that this issue is not caused by a flaw in the Direct Send feature of Microsoft 365 itself. Instead, the root cause lies in misconfigured MX records, where email routing is not correctly pointed to Microsoft services or where anti-spoofing policies are too permissive.
Organizations that route email directly through Microsoft systems benefit from built-in impersonation detection and additional security layers that help mitigate these attacks.
Microsoft’s Security Recommendations
To reduce risk, Microsoft strongly advises organizations to take the following steps immediately:
- Configure SPF with a strict hard fail policy
- Set DMARC enforcement to reject mode
- Implement multi-factor authentication, preferably passwordless MFA
These measures help create a stronger security barrier against increasingly sophisticated and realistic phishing attacks. As cyber threats continue to evolve, Microsoft stresses that proactive configuration and enforcement remain critical to protecting both corporate data and financial assets.
Source: Microsoft